Iran International Reveals Tehran-Based Cyber Group Targeting Israeli Hospital
Iran International can reveal that the Islamic Republic’s Intelligence Ministry conducts cyberattacks against Israeli civilian targets via a cover tech company.

Iran International can reveal that the Islamic Republic’s Intelligence Ministry conducts cyberattacks against Israeli civilian targets via a cover tech company.
The cyber group “Black Shadow” (“Saye-ye Siah” in Persian), which targeted Ziv Medical Center in the northern Israeli city of Safed in November is in fact a tech company which works under the registered name of “Raahkarha-ye Fanavari-e Etela’at-e Jahatpardaz.”
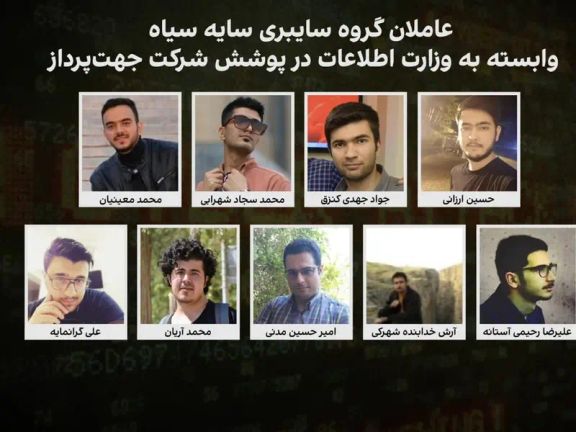
According to Iran International’s investigative journalist Mojtaba Pourmohsen, the two operational offices of the “Black Shadow” cyber group are located in Tehran.
The website of the company states that a group of “faithful and committed youth” has launched it in line with “The Second Step of the Revolution.”
The Second Step of the Revolution was a statement issued by Ali Khamenei, Iran’s Supreme Leader, in 2019, on the 40th anniversary of the Islamic revolution. It provides “instructions” on how to progress the revolution and its ideas.
The company has not yet responded to Iran International’s request for comment.
Israel’ National Cyber Directorate announced on December 18 that the Islamic Republic and its proxy group Hezbollah were behind the cyberattack on Ziv Medical Center.

“The attack was stopped at an early stage, thereby preventing the attempt by Iran and Hezbollah to harm the functioning of the hospital and the potential for humanitarian harm to civilians,” read a statement by the directorate, further admitting that “the attackers managed to take materials from the hospital and started posting them on social networks.”
According to Iran International’s report, Iran-backed “Black Shadow” also targeted Israel’s tech sector and higher education facilities for 10 months in 2022 to pave the way for the Ministry of Intelligence to steal identity information and sensitive data in a cyberattack.
The group used Wiper malware to erase their tracks in the operation, the report added.
“Black Shadow” is also known by such other names as “AGRIUS” and “Pink Sandstorm.”
Earlier in November, Microsoft’s Threat Analysis Center (MTAC) reported that Iran has intensified its cyberattacks and influence operations since 2020, targeting Israel and other countries. The report also warned that Iran, Russia and China are likely to plan to influence the upcoming elections in the United States and other countries in 2024.
In December, Iran-linked hackers targeted a water facility in the rural area of County Mayo in Ireland, leaving the residents without water for two days. The attack was carried out by pro-Iran Cyber Av3ngers group which claimed that the facility was attacked because it used an Israeli-made piece of equipment.
Last week, Assistant Commissioner Matt Jukes, the UK’s head of counter-terrorism policing, announced that a new unit was established in the British police to deal with threats posed by the Islamic Republic of Iran, Russia and China ahead of the UK’s general election.
The unprecedented volumes of online misinformation have raised concerns among the British security officials ahead of the election. Just last year, Britain’s Home Secretary called Iran the country’s number one threat, with the head of MI5 revealing multiple plots foiled on UK soil since 2022.