Iranian Hackers Target Israeli And UAE Defense Firms

A gang of hackers linked to Iran is targeting aerospace and defense firms in Israel and the UAE, according to Google’s security arm.

A gang of hackers linked to Iran is targeting aerospace and defense firms in Israel and the UAE, according to Google’s security arm.
The group named UNC 1549 – also known as Smoke Sandstorm and Tortoiseshell – have been using a variety of tactics to breach corporate security.
These include ‘spear fishing’ – sending links that appear to relate to a targeted individual’s interests – and ‘watering hole attacks’, in which hackers infect websites they believe someone to visit regularly.
UNC 1549 is known to be linked to the Iranian Revolutionary Guard Corps (IGRC).
According to Jonathan Leathery, principal analyst for Mandiant, the group's tactics make detection challenging: "The most notable part is how illusive this threat can be to discover and track — they clearly have access to significant resources and are selective in their targeting."
Microsoft has previously observed a shift in tactics by Iranian threat groups, particularly targeting IT services firms as a means to infiltrate government networks. Smoke Sandstorm, for instance, compromised a Bahrain-based IT integrator in 2021, indicating a broader strategic agenda.
Initially concentrating on IT service providers, UNC1549 has broadened its scope to encompass aerospace and defense sectors. Its operations transcend the Middle East, suggesting potential links to cyberattacks in Albania, India, and Turkey.
"The intelligence collected on these entities is of relevance to strategic Iranian interests, and may be leveraged for espionage as well as kinetic operations," Google wrote. "This is further supported by the potential ties between UNC1549 and the Iranian IRGC."
Companies are urged to enhance cybersecurity measures, including blocking untrusted links and providing comprehensive awareness training to employees.

The crew of an unflagged ship allegedly smuggling missile parts to Houthi rebels were talking by satellite phone to Revolutionary Guard members, according to an FBI affidavit.
The revelation comes as the captain and three other men from the dhow are due to appear in a federal court in Virginia on Tuesday.
The vessel was intercepted by US naval forces in January in the Arabian Sea amid continuing Houthi attacks on shipping in the region. Two American Navy SEALs drowned in the operation.
The captain, Pakistani national Muhammad Pahlawan, refused to slow the ship when the US Navy began its boarding attempt.
Instead he “shouted for the crew to burn the boat before the Navy could board it,” according to court documents filed in the federal court in Richmond.
Upon searching the vessel, US forces seized Iranian-made weaponry consistent with Houthi attacks, marking the first confiscation of such weapons since the current series of attacks on shipping began in November.
“Initial analysis indicates these same weapons have been employed by the Houthis to threaten and attack innocent mariners,” an FBI agent wrote, quoting Central Command.
Crew members were in communication with a member of Iran’s Revolutionary Guard via satellite phone, according to the FBI.
Pahlawan and the other crew membesr, Mohammad Mazhar, Ghufran Ullah, and Izhar Muhammad, face charges of attempting to smuggle missile components and providing false information. They are accused of misleading authorities about the ship's origin and cargo.
Prosecutors are expected to push for their detention without bond.
Their legal representatives have yet to comment on the case. A further 10 crew members are being detained as material witnesses under federal law.
Iran sponsors the Houthis, providing funding, weapons, and even direct support on the ground. While Iranian officials claim the Houthis operate independently, recent events suggest Iran can influence their actions, as seen in Syria and Iraq.

One of the oddities in Iranian elections over the years is the dwindling presence of clerics in parliament, while the regime shifts towards greater ideological rigidity and less tolerance.
When questioned about the absence of clerics on his candidate list for Tehran, Ali Motahhari, a former deputy speaker of the Majles (parliament) and current candidate, responded candidly. He explained, "There was no deliberate exclusion of clerics from our list. However, among the nominated clerics, we couldn't find anyone who would add more depth or interest to our lineup."
Motahhari, the son of Morteza Motahhari, a prominent ideologue of the Islamic Republic and a cleric himself, has long been known as a staunch defender of the regime's policies, including obligatory hijab. However, he has recognized a notable shift in the preferences of voters participating in the sham elections, indicating a declining demand for clerical representation in parliament.
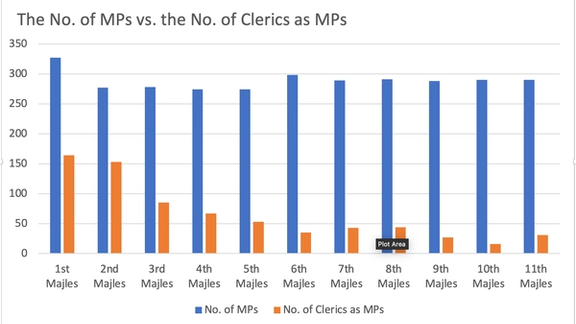
The diminishing support for clerics as parliamentary representatives has been a persistent trend in the Islamic Republic over the years. In the early years of the regime, during the first Majles (1980-1984), over 50 percent of the seats were occupied by clerics.
However, this proportion dwindled significantly to just 5.5% (16 out of 290 seats) in the tenth Majles (2016-2020). This decline has been evident irrespective of whether the majority voted for the reformist or principlist camp or how the Guardian Council handled candidate disqualifications.
Why is this phenomenon occurring in a regime where clerics hold significant sway in politics and are pervasive throughout society? Several social trends may shed light on the declining representation of clerics in parliament.
Firstly, government incompetence plays a significant role. Across various facets of life, public services and infrastructure development have faltered and deteriorated. According to a confidential survey conducted by the Ministry of Islamic Guidance and Culture in 2023, a staggering 73 percent of Iranians, in a confidential survey conducted by the government, expressed the view that clerics should retreat to their mosques and relinquish their involvement in government affairs.
This marked a notable increase from about 31 percent recorded in 2015. This shift in public sentiment has been a gradual trend within Iranian society spanning over four decades.
Another trend is the de-Islamization of society. Despite the regime's efforts to enforce Islamic practices through incentives and penalties, society has moved in the opposite direction.
The Mahsa Movement of 2022 can be seen as a national and social response to the stringent imposition of Sharia law in the public sphere. Iranians are holding Shia clerics accountable for these stringent regulations and oppressions, and as a result, they advocate for reduced clerical influence in the government.

The third trend involves the gradual erosion of public trust in Shia clerics. Prior to the 1979 Revolution, clerics enjoyed some of the highest levels of public trust compared to other societal groups. However, according to the same confidential survey, approximately 56 percent of respondents now express little to no trust in the clergy, while about 25 percent still hold some level of trust in them. Another 18 percent fall somewhere in the middle of the spectrum. Even in Qom, the primary base of Shia clerics, 51 percent of individuals exhibit limited or very limited trust in this group. This marks a significant decline.
On the top of the list for public trust now are physicians by 73 percent and public school teachers by 60 percent.
The fourth trend pertains to an increasing disillusionment with government propaganda permeating every aspect of life. The religious establishment spearheads the government's indoctrination efforts across various sectors including sports, arts, public education, universities, media, and governance. This propaganda campaign, funded by billions of dollars annually allocated to the Shia clergy, has left the public weary of being force-fed such rhetoric.
In response, wherever possible, the public vehemently expresses its disdain for this manipulation. During election periods, this sentiment manifests in two distinct ways: a significant portion of the population opts to abstain from voting altogether, while those who do participate tend to favor non-clerical candidates. Unfortunately, the regime has yet to heed this message.
However, the composition of the Majles, whether predominantly clerical or not, holds little sway over its function within the system governed by the Guardian Jurist. With its oversight powers effectively neutered, the Majles has been relegated to a ceremonial role, while authority lies with 15 councils such as the Expediency Council and Supreme Council of Cultural Revolution, which regularly legislate.
Consequently, the dwindling presence of clerics in the Majles has negligible impact on the performance of this beleaguered institution. What truly matters is the shift in public sentiment: not only are people disillusioned with clerics' ability to improve their lives, but they also harbor a conviction that their influence may exacerbate their circumstances.

Iran's assassination threat against two US former national security advisers has been countered by a $12m-a-year Secret Service operation, official papers reveal.
John Bolton and Robert O’Brien, who served under President Trump, are believed to have been targeted by Tehran in revenge for the killing in 2020 of Qassem Soleimani.
Iran has openly threatened to abduct and assassinate former Trump administration officials in retaliation for the death of the IRGC Commander.
Newly unveiled documents, obtained through a Freedom of Information Act request by CBS News' "60 Minutes," detail the extensive protection measures implemented for Bolton and O'Brien, who continued to receive Secret Service security long after their tenure in the Trump administration had ended.
The documents, submitted to Congress by the Department of Homeland Security (DHS) and signed by DHS Secretary Alejandro Mayorkas, outline comprehensive security arrangements.
These include dedicated special agents offering round-the-clock protection covering residences, workplaces, and both domestic and international travel.
The need for heightened security for Bolton and O'Brien was prompted by credible threats emanating from Iran, although the documents do not explicitly mention the country.
The revelation underscores the escalating tensions between Iran and former members of the Trump administration, with Iran openly targeting individuals as retaliation for past actions.
The disclosed figures reveal that for a ten-month period, expenses related to protecting Bolton amounted to $4,934,963, while those for O'Brien totaled $5,778,713 over a year-long span. Additional non-payroll expenses, such as foreign travel costs and equipment rentals, contributed to the substantial overall expenditure.
US law enforcement also protects Iranian dissidents and journalists in America due to credible threats from Iran.
British police have formed a unit to counter threats from Iran, China, and Russia. The new police unit has prevented a number of Iranian abduction and assassination plots.

An Iranian satellite is to be launched into space from Russia on Thursday, Tehran’s information and communications minister has announced.
The Pars 1 carries a 15-meter camera enabling it to send high-resolution images of surface locations from its orbit 500km above the earth.
The launch aboard a Soyuz rocket will raise fresh concerns about the deepening security alliance between Moscow and Tehran.
Last month, Iran announced the launch of the Sorayya satellite, utilizing the indigenous Qaem 100 satellite carrier, as part of its space program led by the aerospace division of the Revolutionary Guard Corps (IRGC), which has drawn scrutiny from Western nations.
While Iran maintains that its satellite initiatives are aimed at enhancing communication capabilities, critics argue that the efforts are closely linked with the country's missile development program, both managed by the IRGC.
Announcing the launch of the Pars 1, Information and Communications Minister Issa Zarepour said according to IRNA: "The satellite will be launched by the Soyuz international launcher from Russia in line with the development of space and international interactions with various countries."
Recent US intelligence assessments suggest that such satellite launches could accelerate Iran's timeline for developing intercontinental ballistic missiles, heightening anxieties, particularly in light of Iran's advancing nuclear capabilities.
The US has consistently criticized Iran's satellite launches, citing violations of Security Council resolutions due to perceived connections with its ballistic missile program. Last September, Iran deployed the Noor-3 imaging satellite into orbit, positioned at an altitude of 450 kilometers, utilizing a Qassed launch vehicle.

Israel has raised concerns about Hamas, Hezbollah, and Iran seeking to "unite the fronts" and "inflame the region" during the upcoming Muslim holy month of Ramadan, which begins in two weeks.
“Hamas’s main goal is to take Ramadan, with an emphasis on the Temple Mount and Jerusalem, and turn it into the second phase of their plan that began on October 7,” Israeli defense minister Yoav Gallant said Tuesday. “This is the main goal of Hamas, it is being amplified by Iran and Hezbollah.”
Ramadan is one of the more sacred times for Muslims, when the community comes together in a month of fasting and prayer. It has often been a time of heightened tensions between Israel and Palestinians who seek access to holy sites come but encounter Israeli restrictions and tightened security measures.
Pro-Palestinian rallies are held in some Muslim countries every year on the last Friday of Ramadan, called Quds Day (after the Arabic name of Jerusalem, al-Quds). Iran has been the main force behind promoting the Quds Day as a symbol of continued opposition to Israel.

Gallant was speaking to Israeli commanders responsible for operations in the West Bank, where Palestinians fuming at Israel’s onslaught on Gaza would likely face unprecedented measures put in place by the most far right government in Israeli history.
Israel’s minister for national security Itamar Ben Gvir is seeking to prevent Palestinians from praying at the Temple Mount during Ramadan. He is even considering a ban on Arab Israeli citizens below the age of 70, according to the Israeli newspaper Haaretz.
Gallant seems to be opposed to such measures on the grounds that it could inflame Palestinian feelings. He warns against “Irresponsible statements from people who are supposed to be responsible,” most likely addressing Ben Gvir. “We must not give Hamas what it has not been able to achieve since the beginning of the war and converge the combat fronts.”
More than a hundred days since Hamas rampaged Israeli border areas, the Middle East is still grappling with the repercussions. Thousands of Palestinians have been killed or maimed, although there is no independent exact toll on civilian deaths.
Global trade has been hit by ongoing Houthi attacks on commercial ships in the Red Sea. And Hezbollah continues to exchange fire with Israeli troops across the border almost on a daily basis. The only good news is that Iran 's proxies in Iraq and Syria have gone quiet after several rounds of US airstrikes in response to the killing of three American soldiers last month.
On Tuesday, Hezbollah announced that it had launched several rockets at an Israeli aerial surveillance base. One day earlier, the Israeli military had struck targets at the Bekaa Valley, more than a 100 km from the Israel-Lebanon border, where most of the attacks have been concentrated.
It was a clear escalation in a conflict where both sides have shown some restraint despite regular attacks and retaliations.
The United Nations’ peacekeeping mission in Lebanon, UNIFIL, urged both sides to avoid further escalation, according to Reuters, warning that it had observed a "concerning shift" in the exchanges of fire between Israel and Hezbollah.
Hezbollah is widely believed to be the most powerful non-state actor in the region. It is funded and armed by Iran, reportedly capable of hitting any point in Israel with its vast arsenal of more than a hundred thousand missiles. So far, it has not entered the war, fearing harsh response from Israel perhaps, and is likely to stop its attacks if Israel and Hamas agree to the much-anticipated ceasefire.






